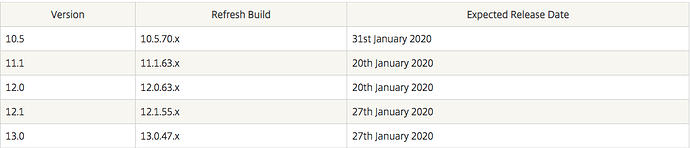
Lots has already been written about CVE-2019-19781 and just how bad of an expoit it is. Citrix has already supplied mitigation steps, but not a fully patched release of the firmware. Just yesterday (January 11th) Citrix updated their documentation with targeted release dates for the new firmware. Spoiler - the fixes are at least 14 days away.
So, you have implemented the remediation as supplied by Citrix, but how do you actually test that the fix is working as expected, and that you are no longer vulnerable. Simple CURL call.
Here you go.
curl https://yourhostname.com/vpn/../vpns/cfg/smb.conf –path-as-is
If you get a 403 response, then you are protected. If you are returned the smb.conf, then you still have work to do.
Below is a Proof of Concept of the attack.