So, due to COVID you now have a bunch of IGEL OS machines sitting in peoples homes, with no real way to manage them remotely, specifically any way to upgrade the firmware. Enter the IGEL Cloud Gateway (ICG). This is a solution that allows you to manage your IGEL thin clients from the same Universal Management Suite (UMS) that you use today, with almost feature parity.
Why do I say almost feature parity? Well you cannot natively upgrade the IGEL OS Firmware using the IGEL Cloud Gateway. You need to configure some kind of storage solution for the updates, and provision them via a profile. In my case, I chose to use Amazon Simple Storage Solution (S3) as it is the easiest, and in our experience the fastest to download the largish (1.5-2.0GB) firmware updates to our thin clients.
Where do begin? I am going to assume that you already have a fully functioning UMS + ICG implementation in place, along with access to the AWS S3 console or CLI.
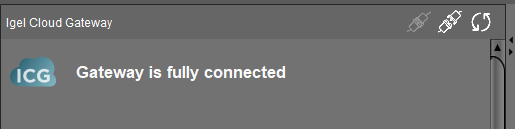
In UMS, if you browse to UMS Administrator - IGEL Cloud Gateway, you should see your ICG. Click on it, and if you see something similar to the picture above, you are good to go. Obviously you will need a thin client that is “registered” to the ICG/UMS configuration. That is out of scope for this article. If you want to learn more about that, let me know, and I can write something up.
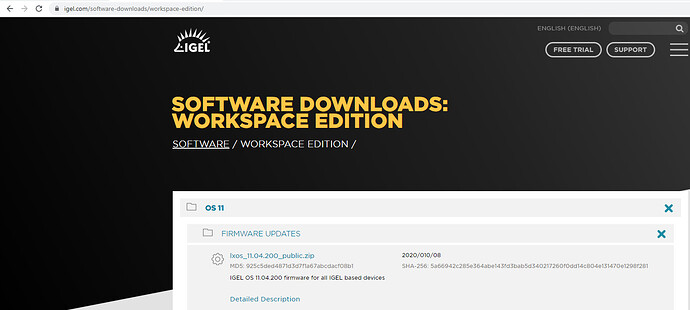
So, onto updating the firmware on a remote thin client. The first thing you need to do is grab a copy of the firmware that you wish to deploy from here. In my case, I am looking for the latest and greatest IGEL OS, so I will be downloading 11.04.200
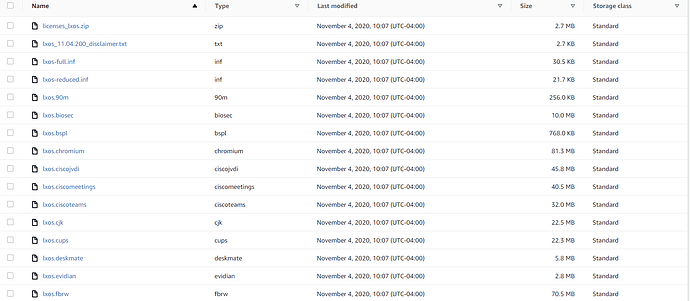
Once the zip file has been downloaded, go ahead an extract it using your favorite archiving tool (shameless plug for 7-zip here). Now we need to head over to the AWS console and create ourselves and S3 bucket for serving up the firmware files. Amazon has this well documented here, so I will not go through that process. Once the bucket has been created, I made a folder to correspond with the firmware version that I will be deploying. Once the version folder has been created, we need to upload all of the files that we extracted earlier into the recently created folder. The firmware files are quite large, so this will take a few minutes. You should now see something like this.
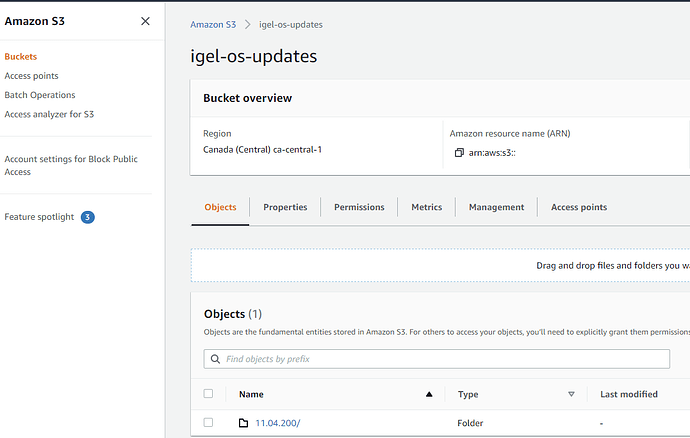
By default all S3 buckets and files are private. We want to serve these up over the internet via HTTPS, so we need to make the bucket, AND the files public. It is not enough to make the bucket public, you must also make the individual files public. Good thing this can be done en masse, as there are are quite a lot of files in the zip file that was downloaded from the IGEL downloads page. My personal best practice is to create a folder in the S3 bucket for each version of the firmware that you plan to use. This makes things much cleaner, and simpler when it is time to deploy a particular firmware version. You can see here that I have created a folder for 11.04.200
So, now that our files are publically available, we need to test that we can access them over the internet. Do do this, simply click on any of the files in the S3 console, which will bring up the properties page. From there you should see the URL of the file. Copy the URL and paste it into a new Incognito tab. If the file opens, or downloads, then you are good to go. If you get an access denied error, then you need to go back to ensure that the files are actually public. Once you have verified public access, keep the URL, as you will need it when you are defining the profile in UMS.
That being said, time to fire up UMS. For these instructions I am using UMS v6.04.110. We need to create a profile that we will assign to our ICG managed thin clients that has the appropriate information for the client in order to download the firmware from AWS S3. Create a new profile, and browse to the following
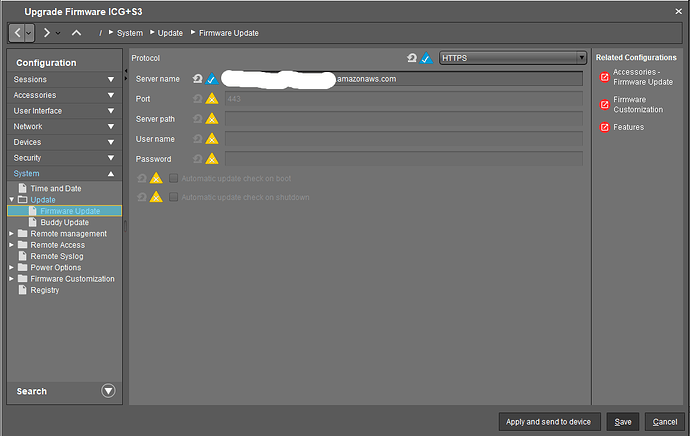
Configuration - System - Update - Firmware Update
From here you will need to change the type to https and enter the base URL of where the files are located. Do NOT include the https:// or the closing slash (/) in the Server Name field, or the download field will fail. Here is a screenshot of my profile, where the files are located.
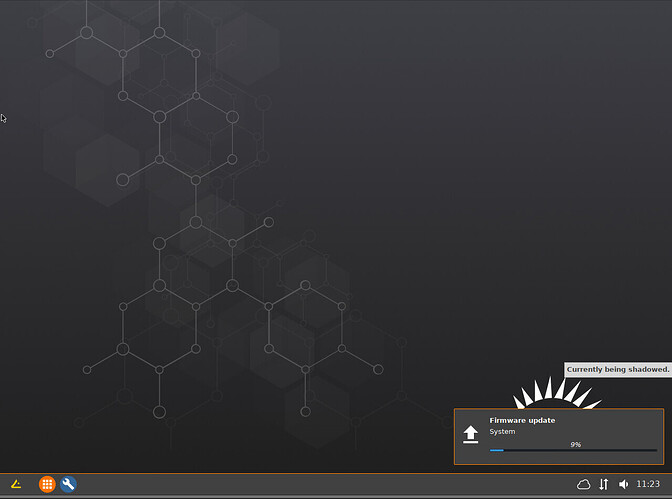
Save the profile, and apply it to the folder where the ICG managed thin clients are located. If you did everything correctly, you should see this magical screenshot.
As you can see in the bottom right of the screen, the thin client is cloud managed, and upgrading the firmware. In the words of Borat, Great Success!